Fuzzing is the art of automatic bug detection. The goal of Fuzzing is to stress the application and cause unexpected behavior, resource leaks, or crashes. Fuzz testing, or fuzzing, is a Black Box software testing technique that basically consists of finding implementation bugs using malformed or semi-malformed data injection in an automated fashion.
A fuzzer is a program that injects automatically semi-random data into a program or stack and detects bugs.
The data-generation part is made of generators, and vulnerability identification relies on debugging tools. Generators usually use combinations of static fuzzing vectors (known-to-be-dangerous values) or totally random data. New generation fuzzers use genetic algorithms to link injected data with observed impacts.The process involves throwing invalid, unexpected, or random data as inputs at a computer. Fuzzers repeat this process and monitor the environment until they detect a vulnerability.
Why Fuzz?
Fuzzing is particularly helpful in locating unknown vulnerabilities that conventional vulnerability management and scanning techniques might not be able to find. By injecting invalid, unexpected, or random data into a program, fuzzers can simulate real-world scenarios and identify potential weaknesses. By identifying and addressing vulnerabilities before malicious actors can exploit them, this proactive approach helps to improve the overall security of software systems.
Tech corporations like Microsoft (OneFfuzz) and Google (oss-fuzz-gen) were early adopters of fuzzing technologies to test their own systems.
The Microsoft OneFfuzz has been archived since November 2023.
What is AI Fuzzing?
AI fuzzing is a cutting-edge method that combines artificial intelligence and machine learning algorithms with conventional fuzzing techniques. AI can automate the process of generating and mutating test inputs, allowing for a more thorough investigation of potential vulnerabilities. AI fuzzing frameworks can analyze a program’s behavior and structure, learn from previous test inputs, and generate new inputs that are likely to cause bugs or vulnerabilities. This advanced approach allows for faster bug identification, reduces reliance on manual test case creation, and improves overall software system security. Using AI, developers can uncover complex and subtle vulnerabilities that would be difficult to detect using traditional fuzzing methods.
In February 2024, Google released its AI Fuzzing framework. (oss-fuzz-gen)
Google wrote in his blog: “Today, we’re releasing our fuzzing framework as a free, open source resource that researchers and developers can use to improve fuzzing’s bug-finding abilities. We’ll also show you how we’re using AI to speed up the bug patching process. By sharing these experiences, we hope to spark new ideas and drive innovation for a stronger ecosystem security.”
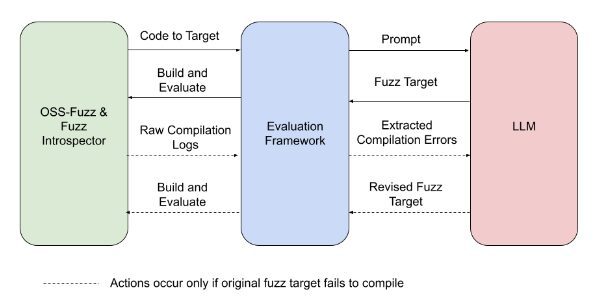
This framework generates fuzz targets with various Large Language Models (LLM) and now supports these models:
- Vertex AI code-bison
- Vertex AI code-bison-32k
- Gemini Pro
- OpenAI GPT-3.5-turbo
- OpenAI GPT-4



